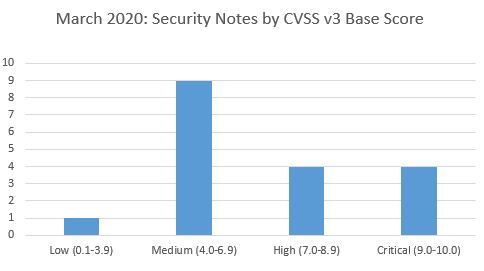
SAP’s security patch day for March 2020 has seen the release of 18 SAP security notes. 9 OSS notes have been classified as medium, 4 OSS notes have been classified as high and 4 as critical, based on CVSS v3.0 Rating.
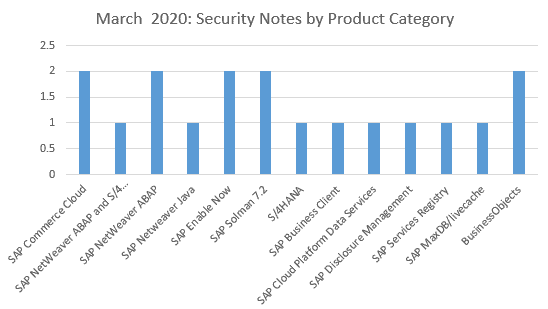
A single security note this month have been found to affect both SAP Netweaver ABAP and s/4HANA, furthermore, 2 vulnerabilities affect each of the following products: SAP Commerce Cloud, SAP Netweaver ABAP, SAP Enable NOW, SAP Solution Manager 7.2 and BusinessObjects. In addition, single vulnerabilities have been identified in each of the following products: SAP Netweaver Java, S/4HANA, SAP Business Client, SAP Cloud Platform Data Services, SAP Disclosure Management, SAP Services Registry and SAP MaxDB/Livecache.
Vulnerabilities: March 2020 Highlights
[CVE-2020-6198] & [CVE-2020-6207] Missing Authorization Checks in SAP Solman Diagnostic Agents (SAP Note 2845377 and SAP Note 2890213)
The diagnostic agent allows connections from unauthorised connections to an insecure server port. This could allow an attacker to perform commands as the SIDadm user of the agent, or to stop or disable monitoring. Within SolMan itself there is exposure of User Experience Monitoring if SSO for this component has not been activated.
An update of the LM-SERVICE component, or an update to SOLMANDIAG 720 is required to remove the exposure. Within SolMan note 2890213 outlines steps to be performed manually to minimise exposure to the exploit.
| [CVE-2020-6198] & [CVE-2020-6207] Missing Authorization Checks in SAP Solman Diagnostic Agents (SAP Note 2845377 and SAP Note 2890213) |
The diagnostic agent allows connections from unauthorised connections to an insecure server port. This could allow an attacker to perform commands as the SIDadm user of the agent, or to stop or disable monitoring. Within SolMan itself there is exposure of User Experience Monitoring if SSO for this component has not been activated.
An update of the LM-SERVICE component, or an update to SOLMANDIAG 720 is required to remove the exposure. Within SolMan note 2890213 outlines steps to be performed manually to minimise exposure to the exploit.
| [CVE-2020-6208] Crystal Reports RPT File Parsing Use-After-Free Remote Code Execution Vulnerability(SAP Note 2861301) |
An attacker could inject code in a file that could be uploaded by a user and opened to perform the attack, resulting in DDOS, or unauthorized execution of commands. Relevant support packages and patches must be applied to resolve the vulnerability.
[CVE-2020-6196] Denial of service (DOS) in SAP BusinessObjects Mobile (MobileBIService)(SAP Note 2826782 )
An attacker able to gain access to the same network as SAP BusinessObjects Mobile could overload the service and render it unresponsive by using specifically crafted payloads in requests. The note provides details for configuring the solution to prevent this vulnerability being exploited.
An attacker able to gain access to the same network as SAP BusinessObjects Mobile could overload the service and render it unresponsive by using specifically crafted payloads in requests. The note provides details for configuring the solution to prevent this vulnerability being exploited.
| [CVE-2020-6203] Path Manipulation in SAP NetWeaver UDDI Server(Services Registry)(SAP Note 2806198)
Services Registry can have the path information provided by users exploited by the insertion of characters used to traverse to the parent directory via an API, if the attacker passes this information as there isn’t currently sufficient validation of the content. Support packages and patches need to be applied to resolve this vulnerability.
[CVE-2020-6209] Missing Authorization check in SAP Disclosure Management (SAP Note 2858044)
SAP’s Disclosure Management doesn’t check the permissions of an authorized user and can result in an escalation of privileges in version 10.1 with a stack version earlier than 1500. Manually install stack 1500 or later to resolve the vulnerability.
[CVE-2018-2450] SQL Injection Vulnerability in SAP MaxDB/liveCache (SAP Note 2660005)
SAP’s MaxDB as used in its livecache solution is open to an SQL injection vulnerability for any installations running on version 7.8.*.* > 7.9.09.08. Any installations running this version of the database software must upgrade to the latest version of 7.9.09.09. |
[CVE-2020-6192] Security updates for the browser control Google Chromium delivered with SAP Business Client (SAP Note 2622660)
SAP Business Client installer includes a packed release of Google Chrome (from release 6.5 PL5) that is the current stable version at the time of install. The note outlines that the version needs to be updated to the latest version to remove the risk of web page exploits.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.







