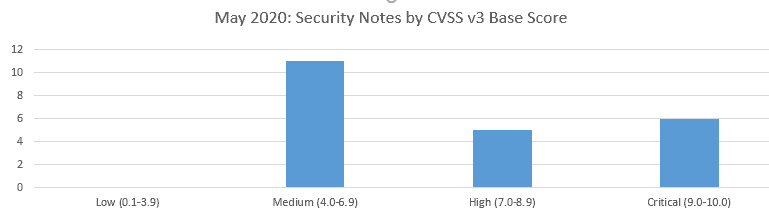
SAP’s security patch day for May 2020 has seen the release of 22 OSS SAP security notes. 11 OSS notes have been classified as medium, 5 OSS notes have been classified as high and 6 as critical based on CVSS v3.0 Rating.
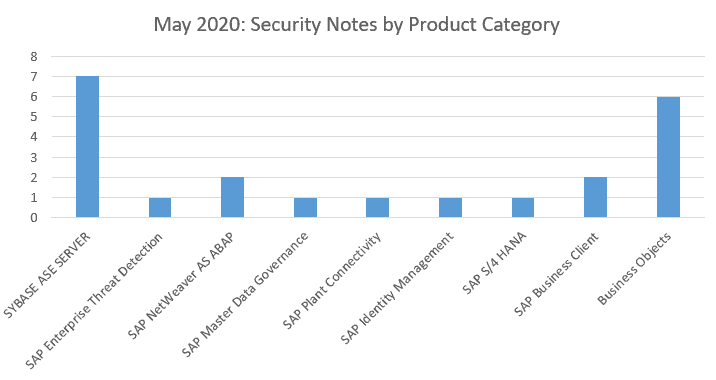
Seven OSS notes have been found this month for the SYBASE, and six for the Business Objects. Another two have been found for the SAP Business Client and another two for the SAP NetWeaver ABAP. A single security OSS note this month has been found to the SAP Enterprise Threat Detection, SAP Master Data Governance, SAP Plant Connectivity, SAP Identity Management and SAP S/4 Hana.
Vulnerabilities: May 2020 Highlights
[CVE-2020-6262] Code Injection vulnerability in Service Data Download (SAP Note 2835979)
Service Data Download (a part of the SAP Solution Manager Plugin) allows an attacker to inject code that can be executed by the application. An attacker could thereby control the behaviour of the application and the whole ABAP system. Implementation of this note should resolve the vulnerability.
Security updates for the browser control Google Chromium delivered with SAP Business Client (SAP Note 2622660)
This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note has been re-released with updated ‘Solution’ and ‘Support Packages & Patches’ information.
[CVE-2020-6242] Missing Authentication check in SAP Business Objects Business Intelligence Platform (Live Data Connect) (SAP Note 2885244)
To enable SAML for Live Data Connect, the documentation requires the user to activate the trusted authentication. In case BIPRWS application server was not protected with a specific certificate, it allows an attacker to log on to the Central Management Console without a password. SAP have now released a fix for this.
[CVE-2020-6248] Code injection in SAP Adaptive Server Enterprise (Backup Server) (SAP Note 2917275)
SAP Adaptive Server Enterprise (ASE) Backup Server does not perform the necessary validation checks for an authenticated user while executing DUMP or LOAD command allowing arbitrary code execution or Code Injection. The issue is fixed by placing validation checks at appropriate place in an SAP ASE version.
[CVE-2020-6219] Deserialization of Untrusted Data in SAP Business Objects Business Intelligence Platform (CR .Net SDK WebForm Viewer) (SAP Note 2863731)Â
Crystal Reports .Net SDK WebForm Viewer allows an attacker with basic authorization to perform deserialization attack in the application, which may lead to code execution upon it.  This note, which we highlighted last month, has been re-released with updated ‘Title’, ‘Symptom’, ‘Other Terms’, ‘Support Packages & Patches’ information.
[CVE-2020-6252] Information Disclosure in SAP Adaptive Server Enterprise (Cockpit) (SAP Note 2917090)
Under certain conditions SAP Adaptive Server Enterprise (ASE) Cockpit allows an attacker to access sensitive and confidential information through local network which would otherwise be restricted. It could be used to get user account credentials, tamper with system data and impact system availability. To fix this issue an update of the SAP ASE Cockpit is needed.
[CVE-2020-6241] SQL Injection vulnerability in SAP Adaptive Server Enterprise (SAP Note 2916927)
SAP Adaptive Server Enterprise (ASE) allows an authenticated user to execute crafted database queries to elevate privileges of users in the system. To fix this issue an update of the SAP ASE is needed.
[CVE-2020-6243] Code Injection in SAP Adaptive Server Enterprise (XP Server on Windows Platform) (SAP Note 2915585)
SAP Adaptive Server Enterprise (XP Server on Windows Platform) does not perform the necessary checks for an authenticated user while executing the extended stored procedure. The XP Server does insufficient error checking for an authenticated user while executing the extended stored procedure. Impacts only Windows platform. This issue is fixed by placing validation checks at appropriate place while executing extended stored procedure.
[CVE-2020-6249] SQL Injection vulnerability in SAP Master Data Governance (MDG) (SAP Note 2908560)
The use of an admin backend report from within MDG allows an attacker to execute crafted database queries, exposing the backend database. Implement the Support Packages and Patches referenced by this SAP Note.
[CVE-2020-6253] SQL Injection vulnerability in SAP Adaptive Server Enterprise (Web Services) (SAP Note 2917273)Â
Under certain conditions, SAP Adaptive Server Enterprise (ASE) Web Services allows an authenticated user to execute crafted database queries to elevate privileges of users in the system. To fix this issue an update of the SAP ASE is needed.
[CVE-2020-6244] Binary planting vulnerability in SAP Business Client (SAP Note 2911801)
SAP Business Client allows an attacker after a successful social engineering attack to inject malicious code as a DLL file in untrusted directories that can be executed by the application. An attacker could thereby control the behaviour of the application. Prerequisite for a successful attack is a rather sophisticated social engineering attack. SAP Business Client will now only load DLL’s from trusted directories.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.










