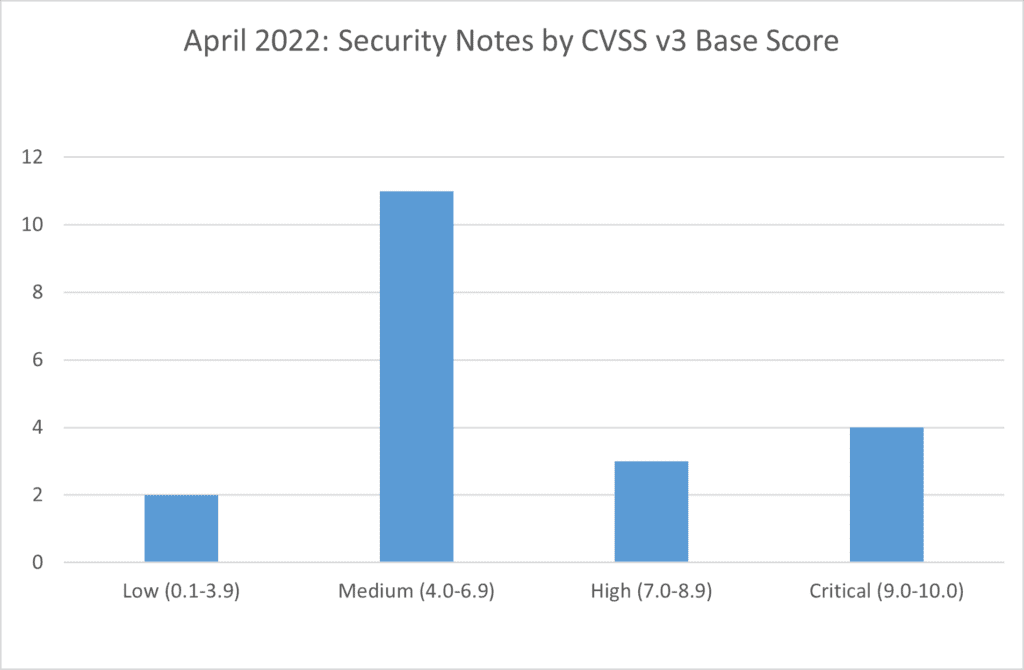
SAP’s security patch day for April 2022 has seen the release of 20 new OSS SAP security notes. 2 notes have been classified as low, 11 notes have been classified as medium, 3 as high and 4 as critical, based on CVSS v3.0 Rating.
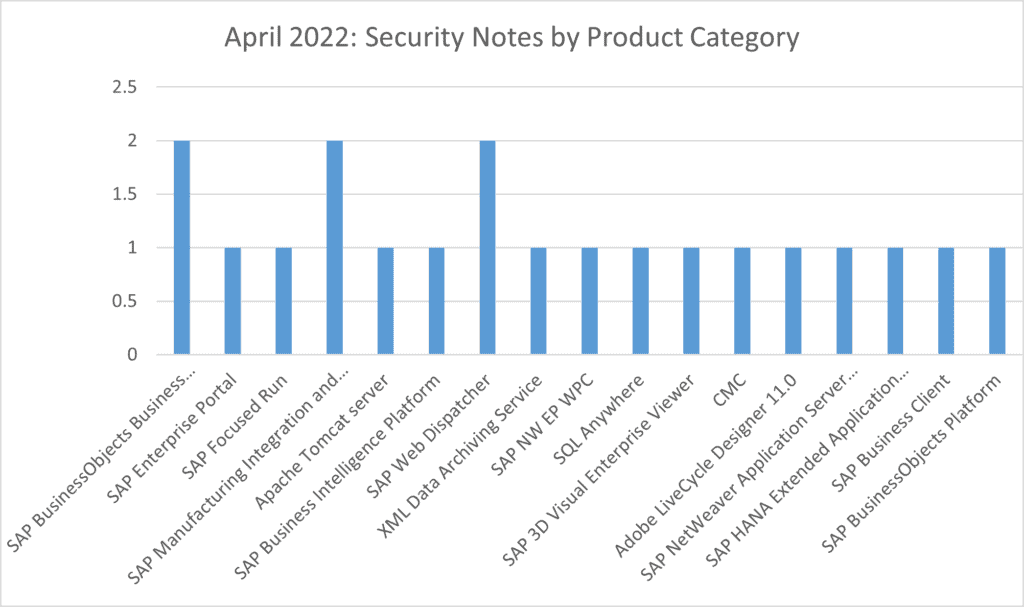
2 notes have been released for SAP BusinessObjects Business Intelligence Platform, SAP Manufacturing Integration and Intelligence and SAP Web Dispatcher. Single notes have been released for SAP Enterprise Portal, SAP Focused Run, Apache Tomcat server, SAP Business Intelligence Platform, XML Data Archiving Service, SAP NW EP WPC, SQL Anywhere, SAP 3D Visual Enterprise Viewer, CMC, Adobe LiveCycle Designer 11.0, SAP NetWeaver Application Server, ABAP and ABAP Platform, SAP HANA Extended Application Services, SAP Business Client and SAP BusinessObjects Platform.
Vulnerabilities: April 2022 Highlights
[CVE-2022-28772] Denial of service (DOS) in SAP Web Dispatcher and SAP Netweaver (Internet Communication Manager) (SAP Note 3111311)
By overlong input values, an attacker may force overwrite of the internal program stack in SAP Web Dispatcher or Internet Communication Manager, which makes these programs unavailable. Patching your Kernel to the latest available version is the recommended fix.
Security updates for the browser control Google Chromium delivered with SAP Business Client (SAP Note 2622660)
From SAP Business Client 6.5 PL5 and above you can use the browser control Chromium for displaying HTML content within SAP Business Client. As this full browser control is delivered and can be installed with SAP Business Client, security corrections for this browser control are shipped with SAP Business Client patches. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, information disclosure etc.
[CVE-2022-26105] Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Enterprise Portal (SAP Note 3163583)
SAP NetWeaver Enterprise Portal is susceptible to script execution attacks by an unauthenticated attacker due to improper sanitization of the user inputs while interacting on the Network. On successful exploitation, an attacker can view or modify information causing a limited impact on the confidentiality and integrity of the application.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.










