This article was originally written in January 2019 and was updated in September 2025 to showcase the new release dates for the upcoming 12 months.
This article covers some FAQs on how SAP addresses vulnerabilities in its software and the best practices for customers to ensure their systems are secure throughout 2026.
How does SAP Address Security Vulnerabilities?
SAP have adopted a monthly patch day to release a batch of SAP security notes that address urgent security vulnerabilities across all of their products. The patch day is on the second Tuesday of every month.
Customers – and their SAP support partners – should review the SAP Security Notes released each month relevant to specific systems, assess the specific risk for each note, and apply the fixes as required promptly after the patch day.
Security issues resolved by a support package are also released monthly as SAP Notes. Still, the fixes are applied in the next support package application and not immediately on the release of the note itself.
Very urgent – so-called ‘zero-day vulnerabilities’ – are occasionally released outside of the regular patch day or support packages for immediate consideration and implementation. These are issued as Hot News by SAP, where a found vulnerability could be – or has been – exploited in the wild with significant impact and should be fixed immediately.
Security Patch Dates for 2025 and Beyond

What are CVE Numbers?
Most security vulnerabilities fixed by SAP in a patch day note are issued with a Common Vulnerabilities and Exposures (CVE) number. These refer to a publicly known vulnerability and take the format of CVE-Year–Number. For example, CVE-2014-0160 refers to the famous heartbleed vulnerability.
MITRE administers the CVE programme, but they have designated SAP as a CVE Number Authority (CNA), meaning SAP issues CVE numbers for reported vulnerabilities.
What do the CVSS v3 Ratings Mean?
The Common Vulnerability Scoring System (CVSS) is an open and cross-vendor framework for describing the characteristics and severity of a software vulnerability.
The CVSS v3 base score between 0 and 10 provides an indication of the severity of the vulnerability.
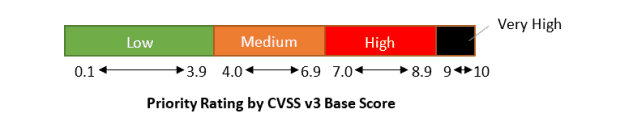
The CVSS v3 base vector gives a more detailed breakdown of the characteristics of the vulnerability, including how it can be exploited and its impact. The scope tracks whether the vulnerability can affect resources beyond the authorisation authority (changed scope, such as escaping a virtual machine) or only within one authority (unchanged scope).
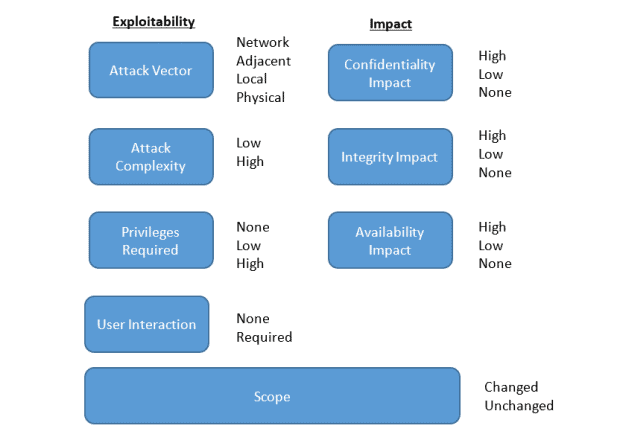
SAP provides the CVSS rating of both the base score and base metric for all vulnerabilities fixed by patch day notes that customers can use to prioritise and understand a particular vulnerability.
How Can I Report a Vulnerability to SAP?
If you find a security vulnerability as an SAP customer, your first port of call should be to log an incident with SAP to report it. If you are an Absoft VAR customer, you should log an incident with Absoft.
SAP ask third parties and security researchers to contact secure@sap.com, with PGP email encryption. You should take care to follow SAP’s current disclosure guidelines and check for the latest information to report a vulnerability.
How Does Absoft Handle Security Vulnerabilities?
Absoft reviews security notes monthly for our managed service customers, with bespoke recommendations provided where an issue is relevant to a specific SAP landscape.
We also publish a monthly digest with a summary of SAP security vulnerabilities that were addressed by SAP that month.
Note that we will never share any details on any vulnerabilities reported in security notes to the general public to comply with disclosure guidelines and to ensure that we do not provide information to attackers before customers have had a chance to patch.









