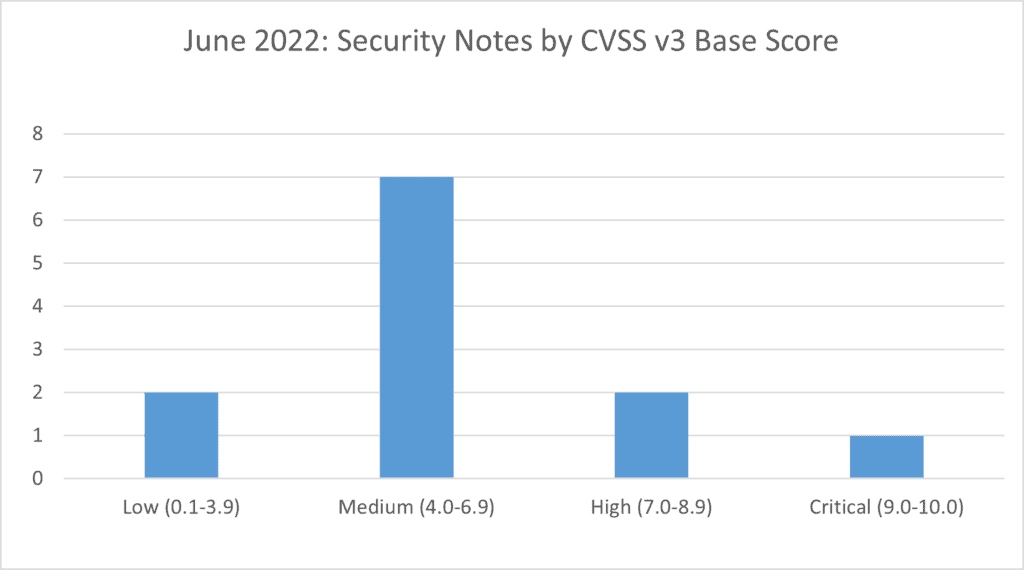
SAP’s security patch day for June 2022 has seen the release of 12 new OSS SAP security notes. 2 notes have been classified as low, 7 notes have been classified as medium, 2 as high and 1 as critical, based on CVSS v3.0 Rating.
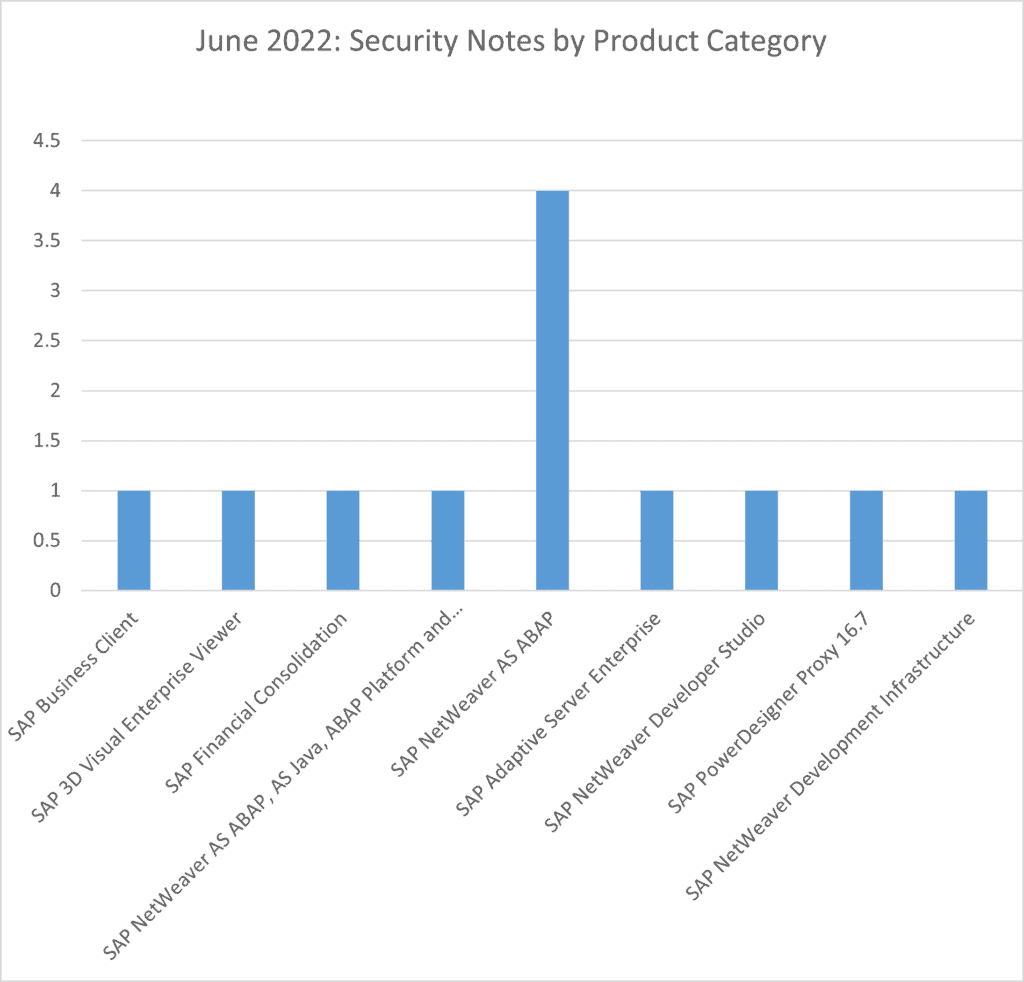
4 notes have been released for SAP NetWeaver AS ABAP. Single notes have been released for SAP Business Client, SAP 3D Visual Enterprise Viewer, SAP Financial Consolidation, SAP Adaptive Server Enterprise, SAP NetWeaver Developer Studio, SAP NetWeaver Development Infrastructure, SAP Power Designer Proxy 16.7 and SHAAM program.
Vulnerabilities: June 2022 Highlights
[CVE-2022-29612] Server-Side Request Forgery in SAP NetWeaver, ABAP Platform and SAP Host Agent (SAP Note 3194674)
SAP NetWeaver, ABAP Platform and SAP Host Agent allow an authenticated user to misuse a function of sapcontrol web functionality (startService) in Kernel which enables malicious users to retrieve information. On successful exploitation, an attacker can obtain technical information like system number or physical address which is otherwise restricted, causing a limited impact on the confidentiality of the application.
[CVE-2022-27668] Improper Access Control of SAProuter for SAP NetWeaver and ABAP Platform (SAP Note 3158375)
Depending on the configuration of the route permission table in file “saprouttab”, Â it is possible for an unauthenticated attacker to execute SAProuter administration commands in SAP NetWeaver and ABAP Platform, from a remote client. For example, stopping the SAProuter, that could highly impact systems availability. SAProuter is designed to restrict administration commands to clients that run on the same host as SAProuter. Administration commands should not be allowed from remote clients. This restriction can be bypassed when a “saprouttab” entry of type “P” or “S” exists with:
- a wildcard (*) for the target host, and
- either a wildcard for the target port or a target port with SAProuter’s own port number (3299 by default).
SAProuter configurations that do not use wildcards for the target host are not affected by the vulnerability.
[CVE-2022-29614] Privilege Escalation in SAP startService of SAP NetWeaver AS ABAP, AS Java, ABAP Platform and HANA Database (SAP Note 3158619)
SAP startService – of SAP NetWeaver Application Server ABAP, Application Server Java, ABAP Platform and HANA Database – on Unix systems, s-bit helper program sapuxuserchk, can be abused physically resulting in a privilege escalation of an attacker leading to low impact on confidentiality and integrity, but a profound impact on availability.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.










