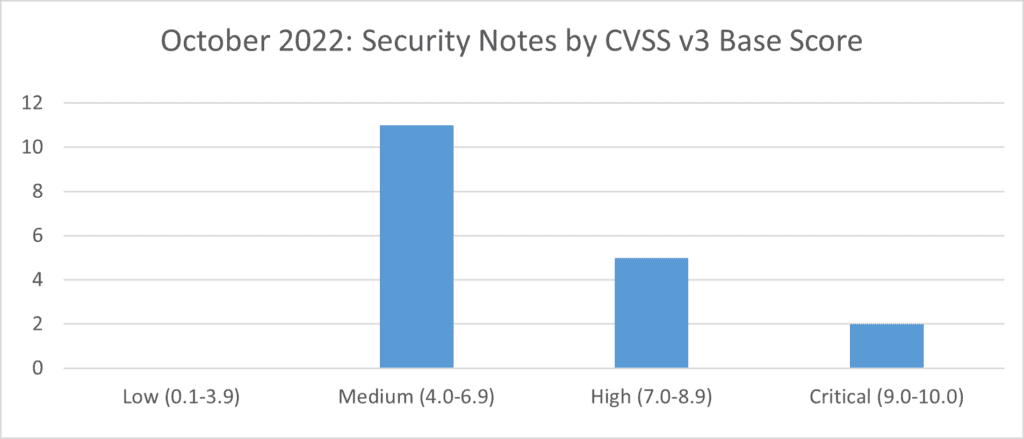
SAP’s security patch day for October 2022 has seen the release of 17 new and 1 updated OSS SAP security notes. 11 notes have been classified as medium, 5 notes have been classified as high and 2 as critical based on CVSS v3.0 Rating.
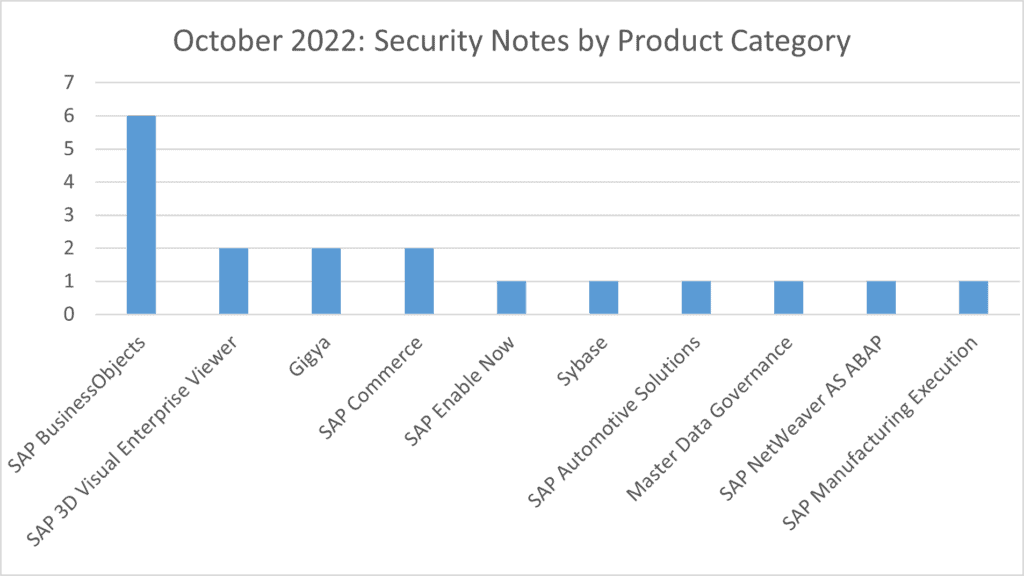
6 notes have been released for SAP BusinessObjects. 2 for SAP 3D Visual Enterprise Viewer, Gigya and SAP Commerce. Single notes have been released for SAP Enable Now, Sybase, SAP Automotive Solutions, Master Data Governance, SAP NetWeaver AS ABAP and SAP Manufacturing Execution.
Vulnerabilities: October 2022 Highlights
[CVE-2022-39802] File path traversal vulnerability in SAP Manufacturing Execution (SAP Note 3242933)
Due to insufficient validation, an attacker is able to manipulate a file path request parameter to view file contents. This may lead to a disclosure of information.
[CVE-2022-41204] Account hijacking through URL Redirection vulnerability in SAP Commerce login form (SAP Note 3239152)
An attacker can use a manipulated URL to change the contents of the SAP Commerce login page. They can inject code to redirect users to their own server, allowing them to steal credentials and hijack accounts.
[CVE-2022-39013] Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Program Objects) (SAP Note 3229132)
Under certain conditions, an attacker can get access to the system’s OS credentials. With OS access an attacker could modify data or make the system unavailable.
[CVE-2022-35299] Buffer Overflow in SAP SQL Anywhere and SAP IQ (SAP Note 3232021)
SAP SQL Anywhere and SAP IQ database servers are vulnerable to a remote unauthenticated stack-based buffer overflow. This can happen if the server is running in debug mode. The attacker can use this vulnerability to modify unauthorized data and could impact the availability of the system.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.










