Overview
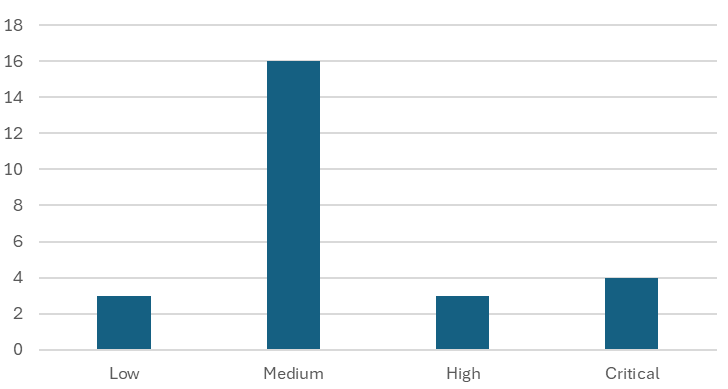
SAP’s security patch day for August 2025 has seen the release of 26 OSS SAP security notes. Four notes have been classified as critical, three as high, 16 as medium, and three as low based on CVSS v3.0 Rating.
Security Notes by CVSS v3 Score
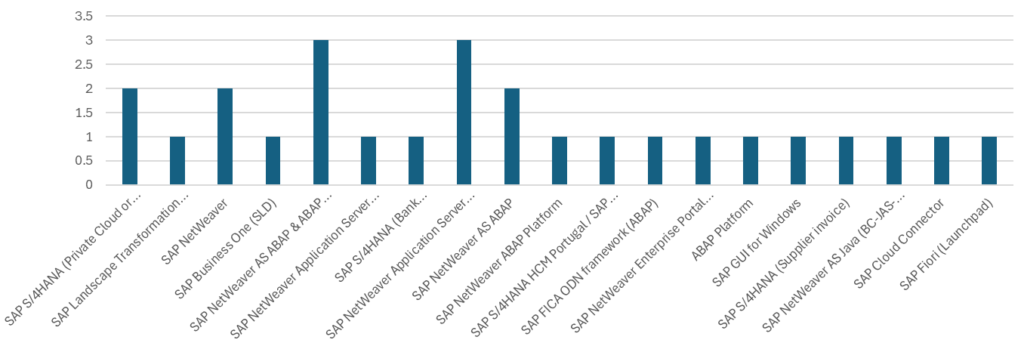
Three notes have been released for:
- SAP NetWeaver Application Server ABAP
- SAP NetWeaver AS ABAP & ABAP Platform
Two notes have been released for:
- SAP S/4HANA (Private Cloud or On-Premise)
- SAP NetWeaver
- SAP NetWeaver AS ABAP
Single notes have been released for:
- SAP Landscape Transformation (Analysis Platform)
- SAP Business One (SLD)
- SAP NetWeaver Application Server ABAP (BIC Document)
- SAP S/4HANA (Bank Communication Management)
- SAP NetWeaver ABAP Platform
- SAP S/4HANA HCM Portugal / SAP ERP HCM Portugal
- SAP FICA ODN framework (ABAP)
- SAP NetWeaver Enterprise Portal (OBN component)
- SAP GUI for Windows
- SAP S/4HANA (Supplier invoice)
- SAP NetWeaver AS Java (BC-JAS-SEC)
- SAP Cloud Connector
- SAP Fiori (Launchpad)
Security Notes by Product Category
Vulnerabilities: August 2025 Highlights
[CVE-2025-27429] Code Injection Vulnerability in SAP S/4HANA (Private Cloud or On-Premise) (SAP Note 3581961) and [CVE-2025-42957] Code Injection Vulnerability in SAP S/4HANA (Private Cloud or On-Premise) (SAP Note 3627998)
SAP S/4HANA allows an attacker with user privileges to exploit a vulnerability in the function module exposed via RFC. This flaw enables the injection of arbitrary ABAP code into the system, bypassing essential authorisation checks. This vulnerability effectively functions as a backdoor, creating the risk of complete system compromise and undermining the confidentiality, integrity, and availability of the system.
[CVE-2025-42950] Code Injection Vulnerability in SAP Landscape Transformation (Analysis Platform) (SAP Note 3633838)
SAP Landscape Transformation (SLT) allows an attacker with user privileges to exploit a vulnerability in the function module exposed via RFC. This flaw enables the injection of arbitrary ABAP code into the system, bypassing essential authorisation checks. This vulnerability effectively functions as a backdoor, creating the risk of complete system compromise and undermining the confidentiality, integrity, and availability of the system.
[CVE-2025-42976] Multiple Vulnerabilities in SAP NetWeaver Application Server ABAP (BIC Document) (SAP Note 3611184)
This Security note addresses multiple vulnerabilities in SAP NetWeaver Application Server ABAP (BIC Document). The vulnerability details, along with their relevant CVE and CVSS information, can be found below:
Memory Corruption [CVE-2025-42976]: SAP NetWeaver Application Server ABAP (BIC Document) allows an authenticated attacker to craft a request that, when submitted to a BIC Document application, could cause a memory corruption error. On successful exploitation, this results in the crash of the target component
Reflected Cross-Site Scripting [CVE-2025-42975]:Â SAP NetWeaver Application Server ABAP (BIC Document) allows an unauthenticated attacker to craft a URL link which, when accessed on the BIC Document application, embeds a malicious script. When a victim clicks on this link, the script executes in the victim’s browser, allowing the attacker to access and/or modify information related to the web client without affecting availability.
[CVE-2025-42946] Directory Traversal Vulnerability in SAP S/4HANA (Bank Communication Management) (SAP Note 3614804)
Due to a directory traversal vulnerability in SAP S/4HANA (Bank Communication Management), an attacker with high privileges and access to a specific transaction and method in Bank Communication Management could gain unauthorised access to sensitive operating system files. This could allow the attacker to potentially read or delete these files, hence causing a high impact on confidentiality and a low impact on integrity.
[CVE-2025-42969] Cross-Site Scripting (XSS) Vulnerability in SAP NetWeaver Application Server ABAP and ABAP Platform (SAP Note 3596987)
SAP NetWeaver Application Server ABAP and ABAP Platform allow an unauthenticated attacker to inject a malicious script into a dynamically crafted URL. The victim, when tricked into clicking on this crafted URL, unknowingly executes the malicious payload in their browser. On successful exploitation, the attacker can access or modify sensitive information within the scope of the victim’s web browser.
About this Review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.









