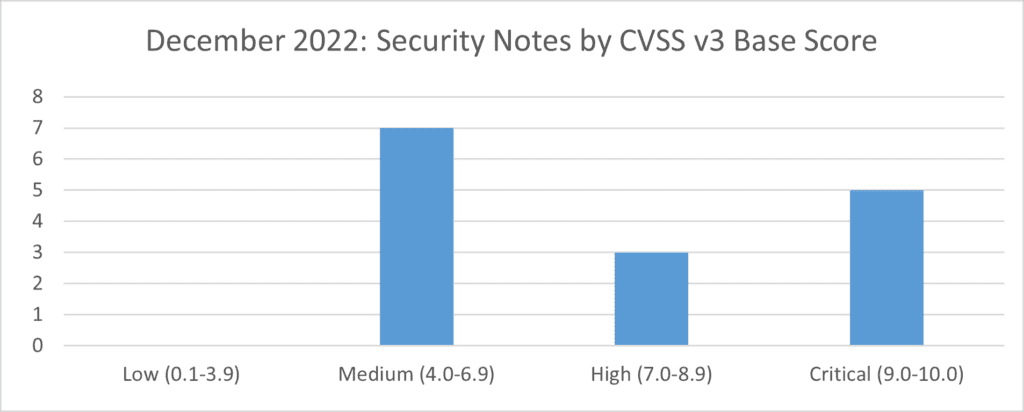
SAP’s security patch day for December 2022 has seen the release of 13 new and 2 updated OSS SAP security notes. 7 notes have been classified as medium, 3 notes have been classified as high and 5 as critical based on CVSS v3.0 Rating.
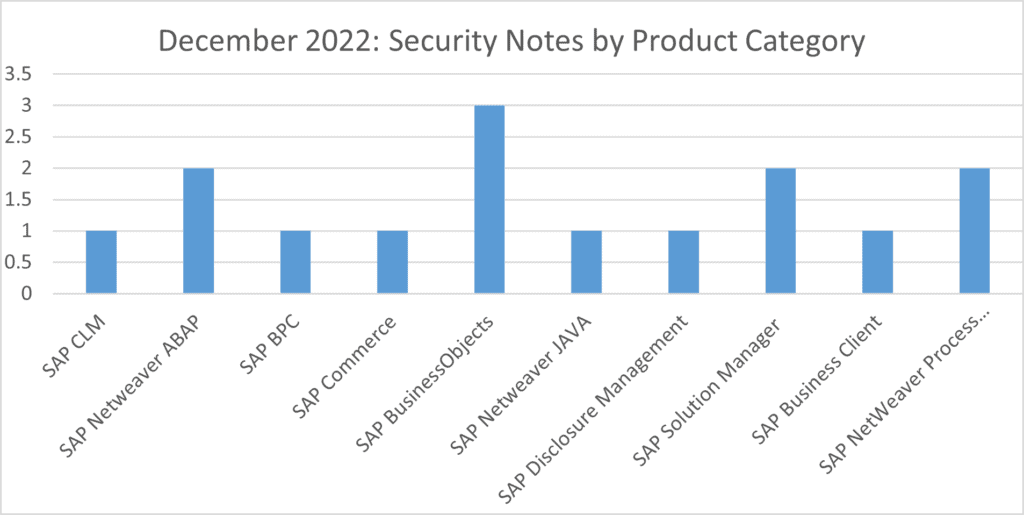
3 notes have been released for SAP BusinessObjects. 2 notes have been released for SAP NetWeaver as ABAP, SAP NetWeaver as JAVA, SAP Solution Manager and SAP Process Integration. Single notes have been released for SAP CLM, SAP BPC, SAP Commerce, SAP Disclosure Manager and SAP Business Client.
Vulnerabilities: December 2022 Highlights
[CVE-2022-41272] Improper access control in SAP NetWeaver Process Integration (SAP Note 3273480)
Due to a programming error, an unauthenticated attacker can attach to an open interface exposed through JNDI by the User Defined Search (UDS) of SAP NetWeaver Process Integration (PI) and make use of an open naming and directory api to access services which can be used to perform unauthorized operations affecting users and data across the entire system. This allows the attacker a full read access to user data and can degrade the performance of the system.
[CVE-2022-41267] Server-Side Request Forgery vulnerability in SAP BusinessObjects Business Intelligence Platform (SAP Note 3239475)
SAP Business Objects platform allows an attacker with normal BI user privileges to upload/replace any file on Business Objects server at operating system level, enabling the attacker to take full control of the system causing high impact on confidentiality, integrity, and availability of the application.
[CVE-2022-42889] Remote Code Execution vulnerability associated with Apache Commons Text in SAP Commerce (SAP Note 3271523)
The Apache Commons Text component used by SAP Commerce performs variable interpolation. This means that the application may be vulnerable to remote code execution or unintentional contact with remote servers if untrusted configuration values are used.
[CVE-2022-41264] Code Injection vulnerability in SAP BASIS (SAP Note 3268172)
Due to the unrestricted scope of the RFC function module, SAP BASIS allows an authenticated non-administrator attacker to access a system class and execute any of its public methods with parameters provided by the attacker. On successful exploitation the attacker can have full control of the system to which the class belongs, causing high impact on integrity of the application.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.










