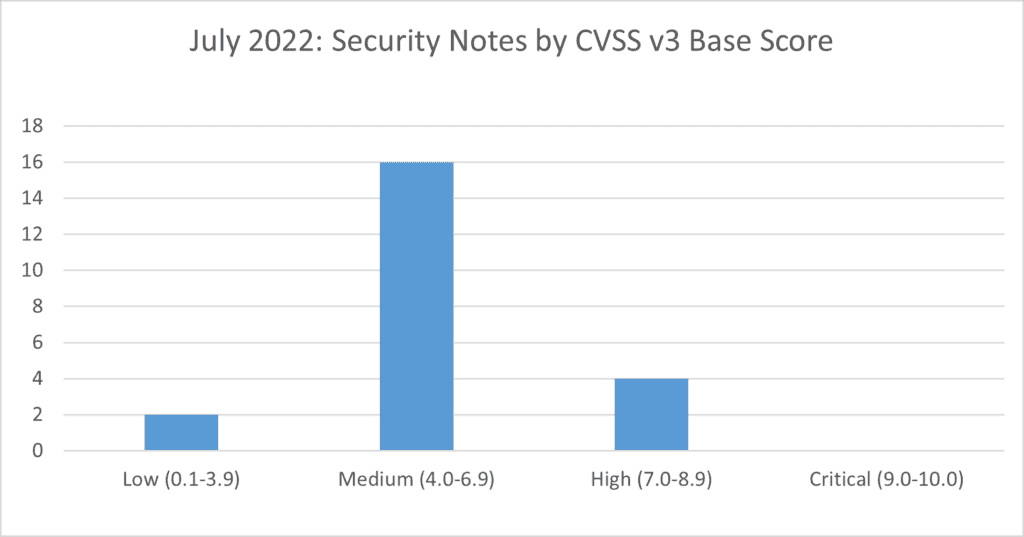
SAP’s security patch day for July 2022 has seen the release of 19 new OSS SAP security notes and 3 updates to existing notes. 2 notes have been classified as low, 16 notes have been classified medium and 4 as high based on CVSS v3.0 Rating.
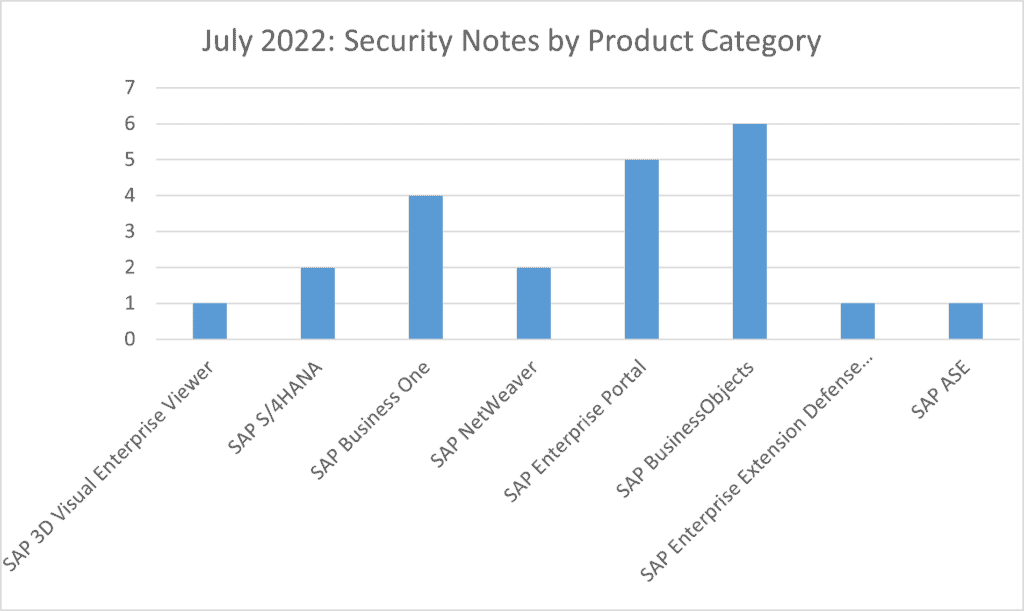
6 notes have been released for SAP BusinessObjects, 5 notes for SAP Enterprise Portal and 4 notes for SAP Business One. 2 notes have been released for SAP S/4HANA and SAP NetWeaver. Single notes have been released for SAP 3D Visual Enterprise Viewer, SAP Enterprise Extension Defense Forces & Public Security and SAP ASE.
Vulnerabilities: July 2022 Highlights
[CVE-2022-35228] Information disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Central management console) (SAP Note 3221288)
SAP BusinessObjects allows an unauthenticated attacker to retrieve token information over the network that should be restricted. By executing this attack, the attacker can completely compromise the application. Patching of BusinessObjects is recommended to better obscure the token.
[CVE-2022-32249] Information Disclosure vulnerability in SAP Business One (SAP Note 3212997)
Under certain circumstances, an attacker can exploit HANA cockpit’s data volume to gain access to highly sensitive information. Patching is recommended although a limited workaround exists.
[CVE-2022-32247] Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Enterprise Portal (SAP Note 3209557)
SAP NetWeaver Enterprise Portal is susceptible to script an execution attack by an unauthenticated attacker due to improper sanitization of user inputs while interacting over the network. On successful exploitation, an attacker can view or modify information causing an impact on the confidentiality and integrity of the application. Patching is recommended.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.










