Overview
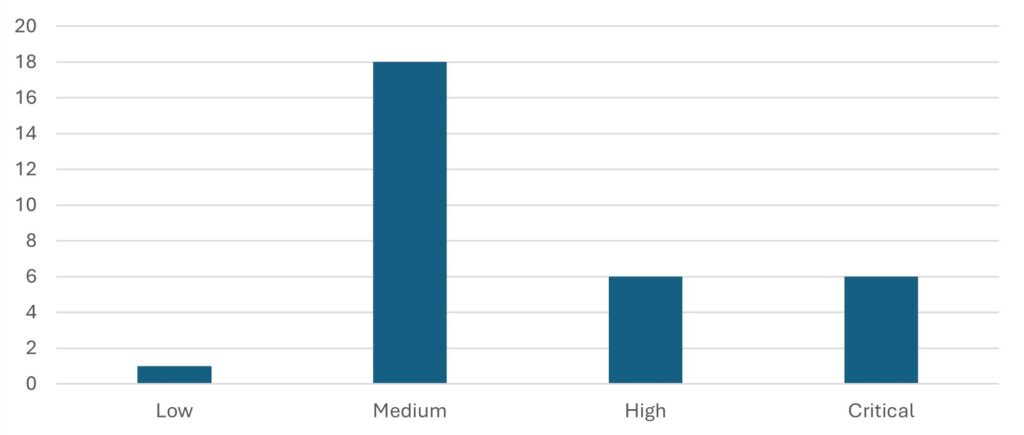
SAP’s security patch day for July 2025 has seen the release of 31 OSS SAP security notes. Six notes have been classified as critical, six as high, eighteen as medium, and one as low based on CVSS v3.0 Rating.
Security Notes by CVSS v3 Score
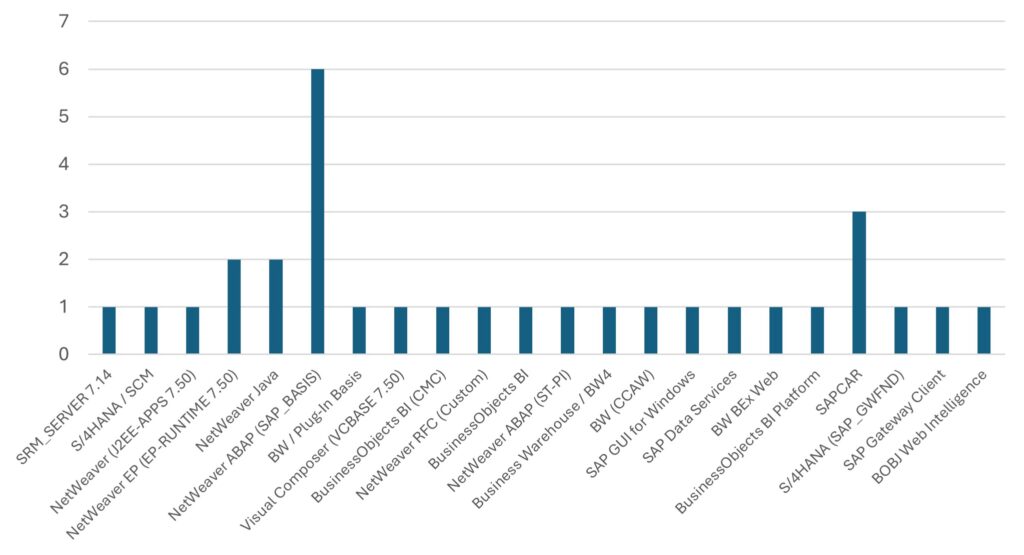
Six notes have been released for:
- NetWeaver ABAP (SAP_BASIS)
Three notes have been released for:
- SAPCAR
Two notes have been released for:
- NetWeaver EP (EP-RUNTIME 7.50)
- NetWeaver Java
Single notes have been released for:
- SRM_SERVER 7.14
- S/4HANA / SCM
- NetWeaver (J2EE-APPS 7.50)
- BW / Plug-In Basis
- Visual Composer (VCBASE 7.50)
- BusinessObjects BI (CMC)
- NetWeaver RFC (Custom)
- BusinessObjects BI
- NetWeaver ABAP (ST-PI)
- Business Warehouse / BW4
- BW (CCAW)
- SAP GUI for Windows
- SAP Data Services
- BW BEx Web
- BusinessObjects BI Platform
- S/4HANA (SAP_GWFND)
- SAP Gateway Client
- BOBJ Web Intelligence
Security Notes by Product Category
Vulnerabilities: July 2025 Highlights
[CVE-2025-42953] Missing Authorisation check in SAP NetWeaver Application Server for ABAP (SAP Note 3623440)
SAP Netweaver System Configuration does not perform necessary authorisation checks for an authenticated user, resulting in the escalation of privileges. This could compromise the integrity and availability of the system, with no impact on its confidentiality.
[CVE-2025-42952] Missing Authorisation check in SAP Business Warehouse and SAP Plug-In Basis (SAP Note 3623255)
SAP Business Warehouse and SAP Plug-In Basis allow an authenticated attacker to add fields to arbitrary SAP database tables and/or structures, potentially rendering the system unusable. On successful exploitation, an attacker can render the system unusable by triggering short dumps on login. This could cause a high impact on availability.
[CVE-2025-42968] Missing Authorisation check in SAP NetWeaver (RFC enabled function module) (SAP Note 3621037)
SAP NetWeaver allows an authenticated non-administrative user to call the remote-enabled function module, which could grant access to non-sensitive information about the SAP system and OS without requiring any specific knowledge or controlled conditions. This results in a minimal impact on confidentiality, with no effect on the integrity or availability of the application.
[CVE-2025-42985] Open Redirect vulnerability in SAP BusinessObjects Content Administrator workbench (SAP Note 3617380)
Due to insufficient sanitisation in the SAP BusinessObjects Content Administrator Workbench, attackers could craft malicious URLs and execute scripts in a victim’s browser. This could potentially lead to the exposure or modification of web client data, resulting in a low impact on confidentiality and integrity.
[CVE-2025-42974] Missing Authorisation Check in SAP NetWeaver and ABAP Platform (SDCCN) (SAP Note 3610056)
Due to a missing authorisation check, an attacker could authenticate as a non-administrative user and call a remote-enabled function module. This could enable access to information that is usually restricted, resulting in a minimal impact on confidentiality.
About this Review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.









