Overview
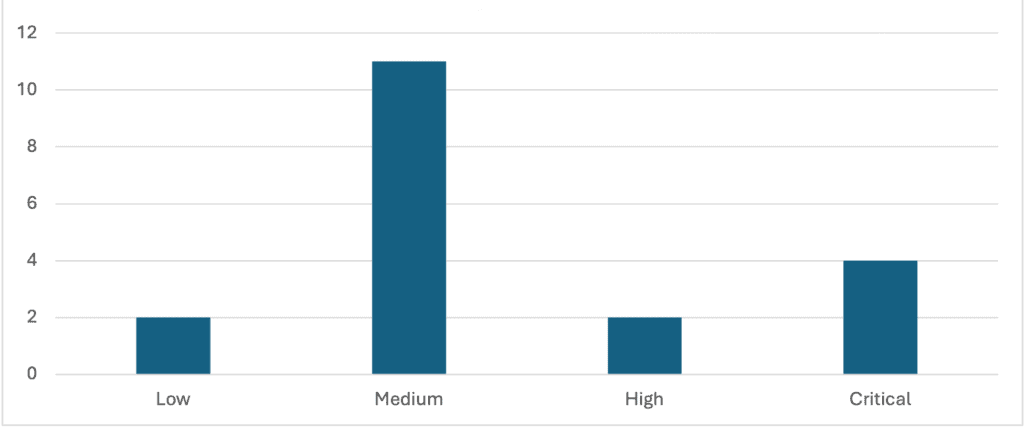
SAP’s security patch day for October 2025 has seen the release of 19 OSS SAP security notes. Four notes have been classified as critical, two as high, eleven as medium and two  as low based on CVSS v3.0 Rating.
Security Notes by CVSS v3 Base Score
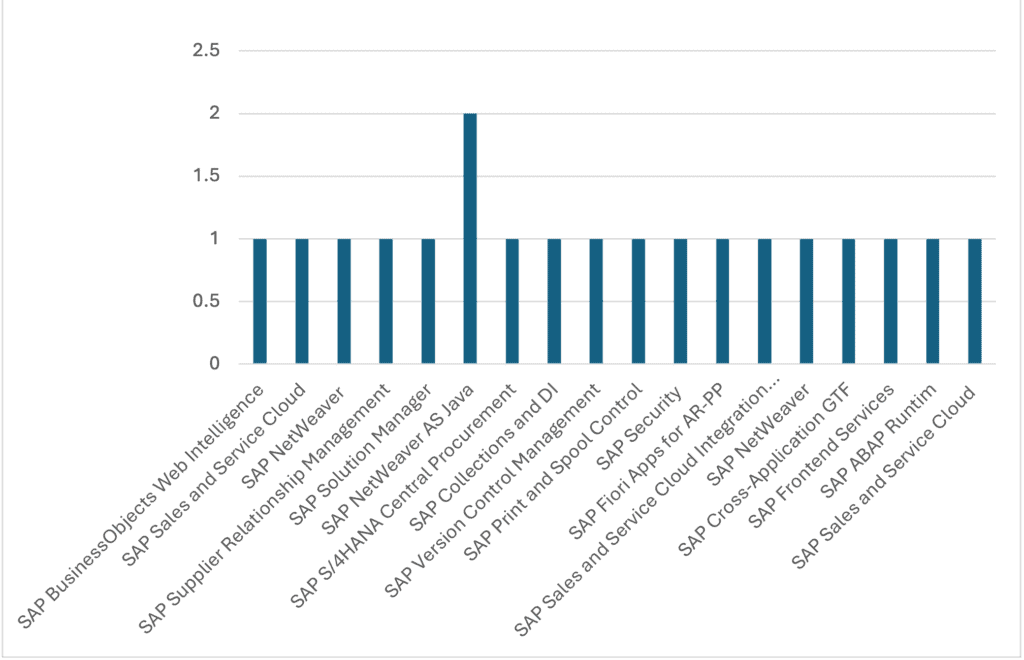
Two notes have been released for:
- SAP NetWeaver AS Java
Single notes have been released for:
• SAP BusinessObjects Web Intelligence
• SAP Sales and Service Cloud
• SAP NetWeaver
• SAP Supplier Relationship Management
• SAP Solution Manager
• SAP S/4HANA Central Procurement
• SAP Collections and DI
• SAP Version Control Management
• SAP Print and Spool Control
• SAP Security
• SAP Fiori Apps for AR-PP
• SAP Sales and Service Cloud Integration Hub
• SAP NetWeaver
• SAP Cross-Application GTF
• SAP Frontend Services
• SAP ABAP Runtime
• SAP Sales and Service Cloud
Security Notes by Product Category
Vulnerabilities: October 2025 Highlights
[CVE-2025-42942]Â Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Application Server for ABAP (SAP Note 3597355Â )
SAP NetWeaver Application Server for ABAP has cross-site scripting vulnerability. Due to this, an unauthenticated attacker could craft a URL embedded with malicious script and trick an unauthenticated victim to click on it to execute the script. Upon successful exploitation, the attacker could access and modify limited information within the scope of victim’s browser. This vulnerability has no impact on availability of the application.
 [CVE-2025-42911] Missing Authorization check in SAP NetWeaver (Service Data Download) (SAP note 3627644)
SAP NetWeaver (Service Data Download) allows an authenticated user to call a remote-enabled function module, which could grant access to information about the SAP system and operating system. This leads to a low impact on confidentiality, with no effect on the integrity and availability of the application
[CVE-2025-42901] Code Injection vulnerability in SAP Application Server for ABAP (BAPI Browser) (SAP note 3652788)
SAP Application Server for ABAP allows an authenticated attacker to store malicious JavaScript payloads which could be executed in victim user’s browser when accessing the affected functionality of BAPI explorer. This has low impact on confidentiality and integrity with no impact on availability of the application.
[CVE-2025-31331] Authorization Bypass vulnerability in SAP NetWeaver (SAP Note 3577131)
SAP NetWeaver allows an attacker to bypass authorization checks, enabling them to view portions of ABAP code that would normally require additional validation. Once logged into the ABAP system, the attacker can run a specific transaction that exposes sensitive system code without proper authorization. This vulnerability compromises the confidentiality.
About this Review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.









