Overview
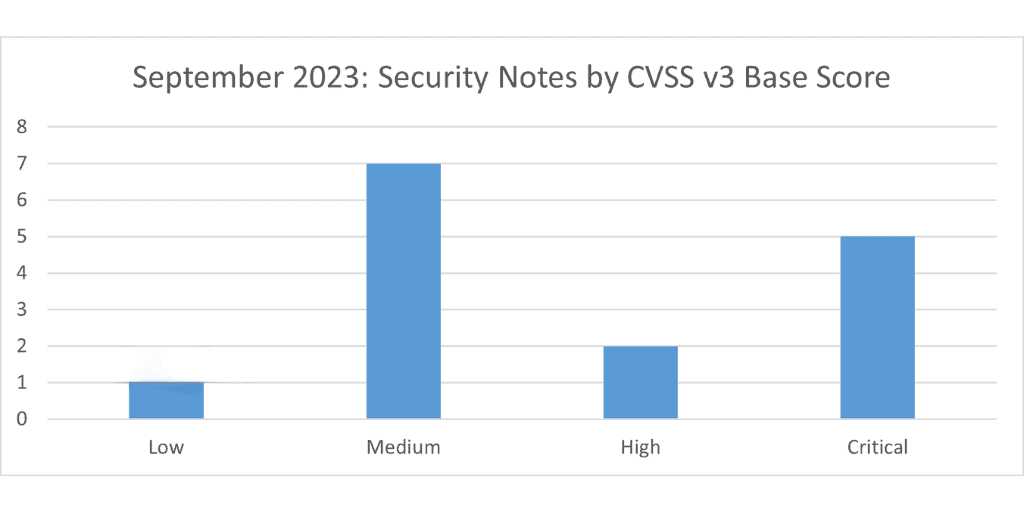
SAP’s security patch day for September 2023 has seen the release of 16 OSS SAP security notes. Overall, five notes have been classified as critical, two as high, seven as medium, and one as low based on CVSS v3.0 Rating.Â
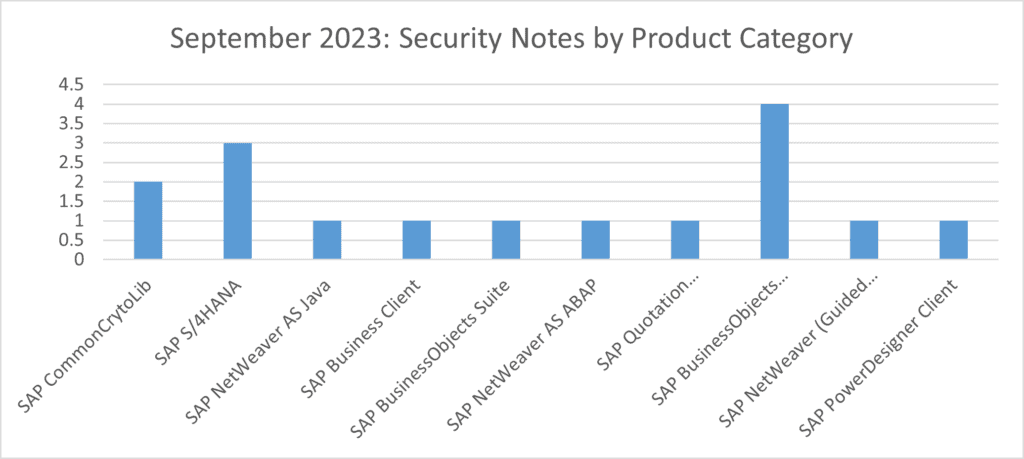
Four notes have been released for:
SAP BusinessObjects Business Intelligence Platform
Three notes have been released for:
- SAP S/4HANA
Two notes have been released for:
SAP CommonCrytoLib
Lastly, single notes have been released for:
SAP NetWeaver AS Java
SAP Business Client
SAP BusinessObjects Suite
SAP NetWeaver AS ABAP
SAP Quotation Management Insurance
SAP NetWeaver (Guided Procedures)
SAP PowerDesigner Client
Vulnerabilities: September 2023 Highlights
[CVE-2023-40309] Missing Authorisation check in SAP CommonCryptoLib (SAP Note 3340576)
SAP CommonCryptoLib does not perform necessary authentication checks, resulting in missing or wrong authorisation checks for an authenticated user and escalating privileges. Depending on the application and the level of privileges acquired, an attacker could abuse functionality restricted to a particular user group and therefore read, modify, or delete restricted data.
[CVE-2023-40308] Memory Corruption vulnerability in SAP CommonCryptoLib (SAP Note 3327896)
An unauthenticated attacker can exploit SAP CommonCryptoLib to craft a request that, when submitted to an open port, causes a memory corruption error in a library, which in turn causes the target component to crash, making it unavailable.
[CVE-2023-40624] Code Injection vulnerability in SAP NetWeaver AS ABAP (applications based on Unified Rendering) (SAP Note 3323163)
An attacker can inject and execute JavaScript code in a web application via SAP NetWeaver AS ABAP (applications based on Unified Rendering). Thus, they could control the behaviour of said web application.
[CVE-2023-40625] Missing Authorization check in Manage Purchase Contracts App (SAP Note 3326361) (SAP Note 3326361)
The Manage Purchase Contracts App does not perform necessary authorization checks for an authenticated user. This as a result allows an attacker to perform unintended actions resulting in the escalation of privileges, which has a low impact on confidentiality and integrity with no impact on the system’s availability.
About this Review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.










