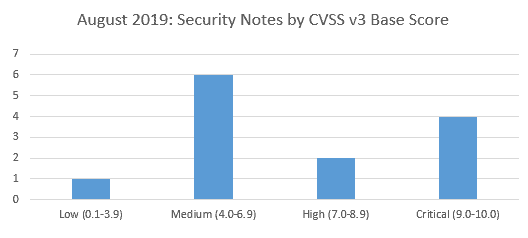
SAP’s security patch day for August 2019 has seen the release of 13 SAP security notes with 2 High and 4 critical CVSS v3.0 Rating.
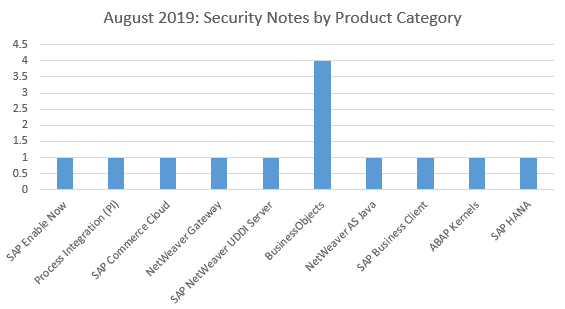
Four of the security notes this month relate to Business Objects and three of these apply to all the 4.x versions of the SAP Business Objects Business Intelligence Platform 4.x, while one applies to the version 4.2 and 4.3. There has been one vulnerability found in each of the following products: SAP Enable Now, Process Integration (PI), SAP Commerce Cloud, NetWeaver Gateway, SAP NetWeaver UDDI Server, NetWeaver AS Java, SAP Business Client, ABAP Kernels and SAP HANA.
 Critical and High Vulnerabilities: August 2019 Highlights
SAP NetWeaver UDDI Server
One vulnerability rated as critical has been identified and corrected in SAP NetWeaver UDDI Server by providing a patch for the software component ESREG-SERVICES. Specifically, a Remote Code Execution vulnerability exists in the Services Registry. Because of this, an attacker can exploit Services Registry potentially enabling them to take complete control of the product, including viewing, changing, or deleting data by injecting code into the working memory which is subsequently executed by the application. It can also be used to cause a general fault in the product, causing the product to terminate.  The solution is to patch the specified component. SAP Note 2800779 describes the problem and solution in more detail.
SAP Business Client
One critically rated vulnerability has been identified with some versions of SAP Business Client 6.5.  SAP Note 2622660  This has occurred because of vulnerabilities discovered in Chromium, which is used as the embedded browser control used by SAP Business Client. You can see more information from Google here.
SAP Commerce Cloud
One vulnerability rated as critical has been identified and corrected in SAP Commerce Cloud by providing a patch for the software component HY_COM. This SAP security note addresses two Remote Code Execution vulnerabilities identified in SAP Commerce Cloud (previously SAP Hybris Commerce). The solution is to patch the specified component latest patch release of SAP Commerce Cloud.  SAP Note 2786035 describes the problem and solution in more detail.
NetWeaver AS Java
AS Java System Overview in SAP NetWeaver Administrator (NWA) allows an attacker to send a crafted request from a vulnerable web application. It is usually used to target internal systems behind firewalls that are normally inaccessible to an attacker from the external network, resulting in a Server-Side Request Forgery vulnerability. The solution is to patch the component LM-CORE. SAP Note 2813811 describes the problem and solution in more detail. After applying the fix on some systems System Overview may display incorrect information about started/failed java server nodes, for example these monitors may show N/A values. The side effect is resolved by applying the settings from SAP Note 2577844
SAP HANA
The other vulnerability rated as high relates to the HANA DB. Specifically, an unauthorized attacker can send a malformed connection request causing Denial of service (DOS), which crashes the indexserver of an SAP HANA instance. As a result, the indexserver is automatically restarted.  The solution is to patch the HANA DB so that it can be to the later version. SAP Note 2798243 provides the fix for this issue.
ABAP Kernels
The other vulnerability rated as high relates to the SAP Kernel (ABAP Debugger) which does not perform necessary authorization checks for an authenticated user, resulting in escalation of privileges. This issue is caused by a bug in the disp+work package of the SAP kernel, which does not validate authorization correctly. The solution is provided as a patch for the disp+work package of the SAP Kernel.  SAP Note 2798743 provides the fix for this issue.
About this review
On the second Tuesday of each month, SAP release security updates to their software products.  At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.