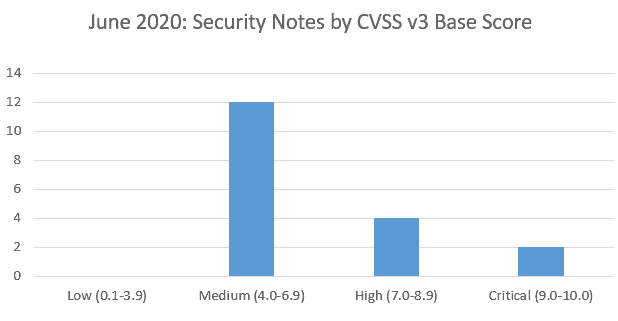
SAP’s security patch day for June 2020 has seen the release of 18 OSS SAP security notes. 12 OSS notes have been classified as medium, 4 OSS notes have been classified as high and 2 as critical, based on CVSS v3.0 Rating.
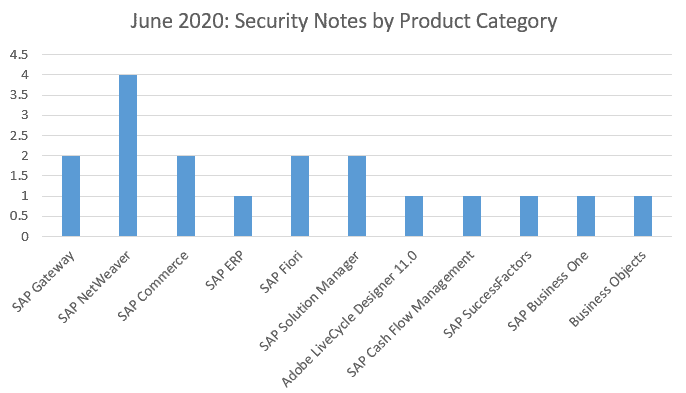
Four OSS notes have been found this month for SAP NetWeaver plus two for SAP Gateway, SAP Commerce, SAP Fiori and Solution Manager. A single security OSS note this month has been found for SAP ERP, Adobe LiveCycle Designer, Cash Flow Management, SAP SuccessFactors, SAP Business One and Business Objects.
Vulnerabilities: June 2020 Highlights
[CVE-2020-6265] Use of Hard-coded Credentials in SAP Commerce and SAP Commerce Datahub (SAP Note 2918924)
SAP Commerce and SAP Commerce Datahub allow attacker to bypass the authentication that has been configured by the system administrator by means of Default Credentials. Â The impact of this could lead to exposure of resources or functionality to unintended users and provide attackers with the possibility of arbitrary code execution.
[CVE-2020-1938] ‘Ghostcat’ Apache Tomcat AJP Vulnerability in SAP Liquidity Management for Banking (SAP Note 2928570)
Due to Apache Tomcat AJP Vulnerability codenamed ‘Ghostcat’, SAP Liquidity Management for Banking could allow remote code execution under some circumstances.
[CVE-2019-0319] Content Injection Vulnerability in SAP Gateway (SAP Note 2752614)
The SAP Gateway allows an attacker to inject content which is displayed in the form of an error message. An attacker could thus mislead a user to believe this information is from the legitimate service when it’s not.
[CVE-2020-6271] Missing XML Validation in SAP Solution Manager (Problem Context Manager) (SAP Note 2931391)
The application Problem Context Manager in SAP Solution Manager does not perform the necessary XML validation, allowing an attacker to consume large amounts of memory, causing the system to crash and could lead to a minor loss of confidentiality.
[CVE-2020-6279] Missing Authorization Check in SAP SuccessFactors Recruiting (SAP Note 2933282)
SAP SuccessFactors Recruiting does not perform necessary authorisation checks for an authenticated user, resulting in escalation of privileges. Missing authorization check are allowing attackers to abuse functionality restricted to a particular user group and read, modify or delete restricted data.
[CVE-2020-6275] Server-Side Request Forgery vulnerability in SAP NetWeaver AS ABAP (SAP Note 2912939)
SAP NetWeaver AS ABAP are vulnerable for Server-Side Request Forgery where in an attacker can use inappropriate path names containing malicious server names in the import/export of sessions functionality and coerce the web server into authenticating with the malicious server. Furthermore, if NTLM is setup the attacker can compromise confidentiality, integrity, and availability of the SAP database.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.










