SAP’s security patch day for November 2019 has seen the release of 15 SAP security notes with 1 High and 4 Critical CVSS v3.0 Rating.
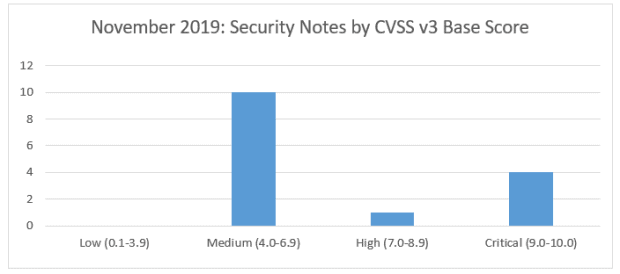
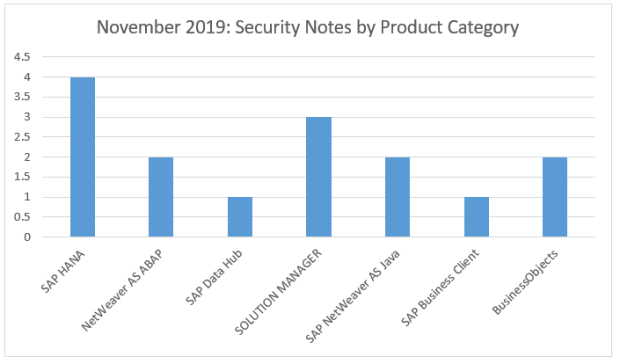
Three of the announced critical vulnerabilities relate to an OS command vulnerability in one of the SAP Solution Manager Java Stack components. This requires the affected component to be patched to the latest level. Another critical vulnerability relates to the version of Google Chrome used by SAP Business Client. The final high vulnerability relates to an XML validation for BI. Two reported vulnerabilities relate to missing authorization checks in the SAP Treasury and Risk management component in on-premise HANA installations. One cross Site Scripting (XSS) vulnerability has been identified in SAP Enable NOW, along with one in SAP Business intelligence. A missing authorization check for ERP and S/4HANA sales (SD-SLS) has been identified. Two Netweaver Java risks, for eCATT and Jco vulnerabilities are reported. A SQL injection vulnerability has been reported for SAP Quality Management in HANA. Finally, a risk for Content Spoofing in UI5 HTTP handler for Netweaver ABAP and a vulnerability for Information Disclosure from SAP Data Hub have been identified.
Vulnerabilities: November 2019 Highlights
Security updates for the browser control Google Chromium delivered with SAP Business Client (SAP Note 2622660)
SAP Business Client installer includes a packed release of Google Chrome (from release 6.5 PL5) that is the current stable version at the time of install. The note outlines that the version needs to be updated to the latest version to remove the risk of web page exploits.
 [CVE-2019-0330] –  Update 1 to Security Note 2808158 OS Command Injection vulnerability in SAP Diagnostics Agent (SAP Note 2823733)
 [CVE-2019-0330] –  Update 2 to Security Note 2808158 – OS Command Injection vulnerability in SAP Diagnostics Agent (SAP Note 2839864)
 [CVE-2019-0330] –  OS Command Injection vulnerability in SAP Diagnostics Agent (SAP Note 2808158)
 All 3 vulnerabilities relate to the OS Command Plugin in the transaction GPA_ADMIN and the OSCommand Console allowing an attacker to inject code that can be executed by the application. An attacker could thereby control the behavior of the application. A new LM_SERVICE patch must be applied to SolMan 7.2 with support packs 6 to 9.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.