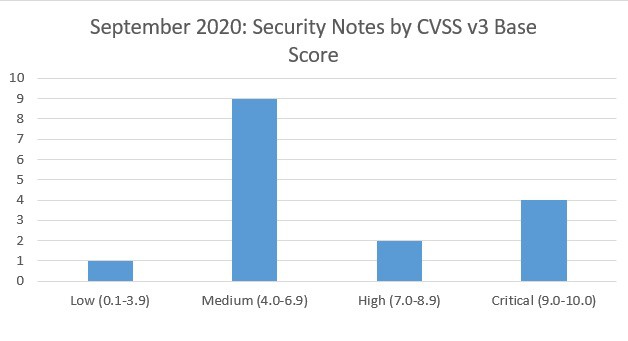
SAP’s security patch day for September 2020 has seen the release of 10 OSS SAP security notes and 6 updates to existing notes. 1 OSS notes has been classified as low, 9 OSS notes have been classified as medium, 2 OSS notes has been classified as high and 4 as critical, based on CVSS v3.0 Rating.
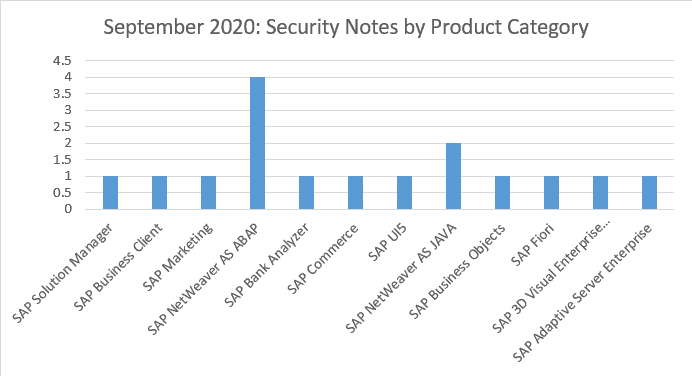
4 OSS notes have been found this month for SAP NetWeaver AS ABAP plus 2 for SAP NetWeaver AS JAVA. Single notes have been released for SAP Solution Manager, SAP Business Clients, SAP Marketing, SAP Bank Analyzer, SAP Commerce, SAP UI5, SAP Business Objects, SAP Fiori, SAP 3D Visual Enterprise Viewer and SAP ASE.
Vulnerabilities: September 2020 Highlights
[CVE-2020-6320] Improper Access Control in SAP Marketing (Mobile Channel Servlet) (SAP Note 2961991)
The servlet reference implementation provided for the Mobile Channel Servlet in SAP Marketing allows an authenticated attacker to invoke certain functions that are restricted. Limited knowledge of payload is required for an attacker to exploit the vulnerability and perform tasks related to contact and interaction data.
Correction instructions are attached to the note and note 2962970 can be used as a workaround.
[CVE-2020-6318] Code Injection vulnerability in SAP NetWeaver (ABAP Server) and ABAP Platform (SAP Note 2958563)
A Remote Code Execution vulnerability exists in SAP NetWeaver and ABAP Platform running on DB4 or Sybase. An attacker can exploit these products potentially enabling to take complete control of the products, including viewing, changing, or deleting data by injecting code into the working memory which is subsequently executed by the application. It can also be used to cause a general fault in the product, causing the products to terminate.
[CVE-2020-6311] Improper Authorization Checks in Banking services from SAP Bank Analyzer and SAP S/4HANA Financial Products (SAP Note 2951325)
Banking services from SAP Bank Analyzer and SAP S/4HANA Financial Products does not correctly perform necessary authorization checks for an authenticated user, that may cause a system administrator to create incorrect authorization proposals on certain fields. This may result in privilege escalation and may expose restricted banking data.
[CVE-2020-6324] Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver AS ABAP (BSP Test Application) (SAP Note 2948239)
BSP Test Application sbspext_table allows an unauthenticated attacker to send polluted URL to the victim. Information available in the victim’s web browser can be read, modified, and sent to the attacker. No sensitive data is disclosed to the attacker as the attack is possible only in test application and service disruption is not possible as part of the impacts.
About this reviewÂ
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.














