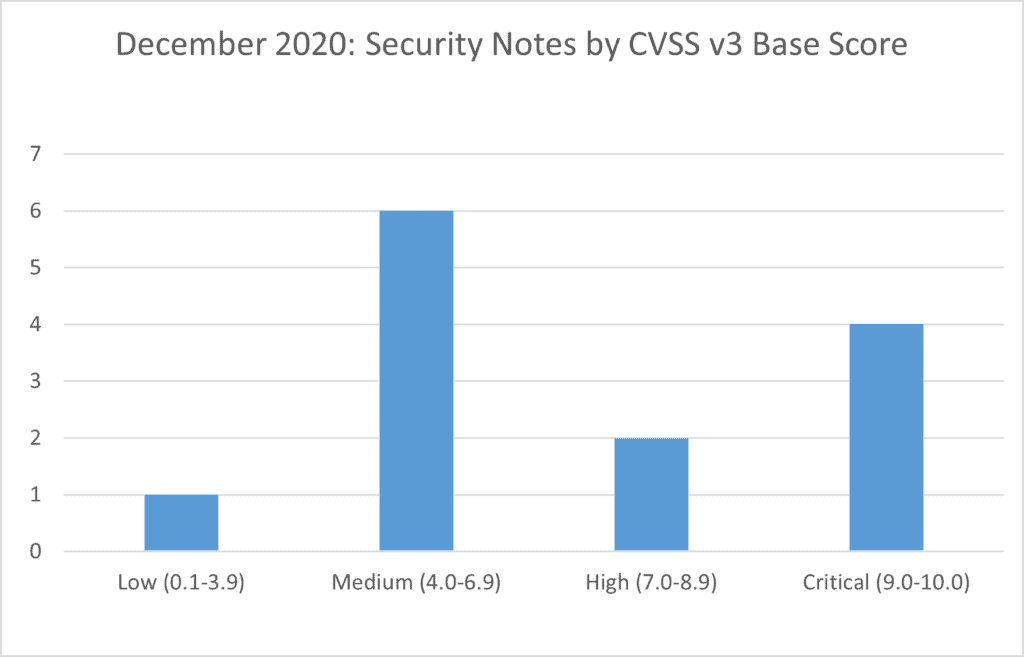
SAP’s security patch day for December 2020 has seen the release of 11 OSS SAP security notes and 2 updates to existing notes. 1 OSS notes have been classified as low, 6 OSS notes have been classified as medium, 2 OSS notes have been classified as high and 4 as critical, based on CVSS v3.0 Rating.
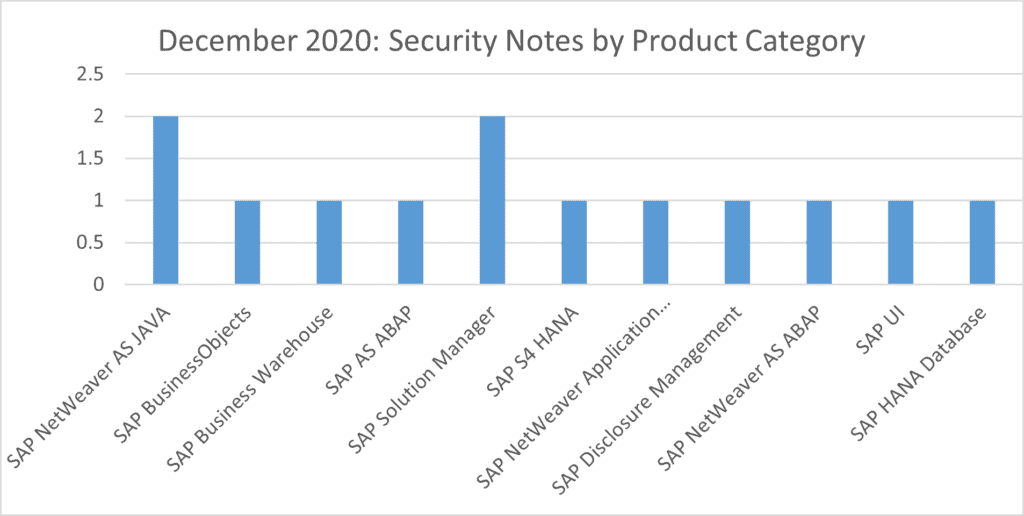
2 OSS notes have been found this month for SAP NetWeaver AS JAVA and SAP Solution Manager. Single notes have been released for SAP BusinessObjects, SAP Business Warehouse, SAP AS ABAP, SAP S4 HANA, SAP NetWeaver Application Server for JAVA, SAP Disclosure Management, SAP NetWeaver AS ABAP, SAP UI and SAP HANA Database.
Vulnerabilities: December 2020 Highlights
[CVE-2020-26829] Missing Authentication Check In SAP NetWeaver AS JAVA (P2P Cluster Communication) (SAP Note 2974774)
The Server Socket, used for accepting P2P connections from the other server nodes in the cluster, was opened to listen on all available network interface controllers. It accepts arbitrary connections even from processes that are outside the cluster and even outside the network segment dedicated for the internal cluster communication. An unauthenticated attacker can invoke certain functions that would otherwise be restricted to system administrators only, including access to system administration functions or shutting down the system completely.
[CVE-2020-26831] Missing XML Validation in SAP BusinessObjects Business Intelligence Platform (Crystal Report) (SAP Note 2989075)
Crystal Report does not sufficiently validate uploaded XML entities. An attacker with basic privileges can inject some arbitrary XML entities leading to internal file disclosure, internal directories disclosure, Server-Side Request Forgery (SSRF) and also denial-of-service (DoS).
[CVE-2020-26838] Code Injection vulnerability in SAP Business Warehouse (Master Data Management) and SAP BW4HANA (SAP Note 2983367)
SAP BW Master Data Management and SAP BW4HANA allows an attacker with high privileges ability to submit a crafted request to generate and execute code without requiring any user interaction. These malicious requests could result in the execution of operating system commands that may completely compromise the confidentiality, integrity and availability of the server and any data or other applications running on it.
[CVE-2020-26838] Code Injection in SAP AS ABAP and S/4 HANA (DMIS) (SAP Note 2983367)
SAP AS ABAP and SAP S/4 HANA allows an authenticated attacker to inject arbitrary code in the application and change the course of execution. Due to lack of input validation, an attacker, who was granted access to execute the function module can inject malicious ABAP code, which will be saved persistently in a report in the ABAP repository.
[CVE-2020-26837] Multiple Vulnerabilities in SAP Solution Manager 7.2 (User Experience Monitoring) (SAP Note 2983204)
Two vulnerabilities have been discovered in SAP Solution Manager 7.2 (User Experience Monitoring).
An authenticated non-administrative user of SAP Solution Manager 7.2 (User Experience Monitoring) can deploy a malicious script which can exploit an existing path traversal vulnerability to fully compromise confidentiality exposing elements of the file system and partially compromise availability by making certain services unavailable.
SAP Solution Manager 7.2 (User Experience Monitoring) does not perform necessary authorization checks for an authenticated user. Due to inadequate access control, a network attacker authenticated as a regular user can use operations which should be restricted to administrators. These operations can be used to deploy a malicious User Experience Monitoring script.
[CVE-2020-26832] Missing Authorization check in SAP NetWeaver AS ABAP and SAP S4 HANA (SAP Landscape Transformation) (SAP Note 2993132)
SAP Landscape Transformation allows a high privileged user to execute an RFC function module to which access should be restricted. This weakness gives attacker the ability to read some sensitive internal information and make vulnerable SAP systems completely unavailable.
About this review
On the second Tuesday of each month, SAP release security updates to their software products. At Absoft, we analyse all of the released security updates and produce this security review, including sending bespoke recommendations for each of our managed service customers.
There is more information on how we handle SAP security updates, including information on SAP’s process, the CVE process and the CVSS base scores in our earlier article on addressing security vulnerabilities in SAP software.







